Data Security Management
With the widespread use of computers and the rapid development of the Internet, society has undergone profound change. Alongside the convenience of information flows come growing concerns over data security. We therefore implement robust protection measures so that convenience is enjoyed only on the premise of security. This is the proper attitude in the information era and the way to meet future challenges.
Shih Wei exercises comprehensive controls over the access, processing, transmission, and retention of customer data, as well as the security of personnel and equipment. Security controls and maintenance measures are applied across application development and maintenance, databases, networks, personal computers, and storage media to prevent theft, loss, or leakage and safeguard customer data.

Information Security Policy
To maintain normal operation of networked information systems, ensure the security of information transmission and transactions, and protect the confidentiality and integrity of data processed by computers, thereby ensuring the security of data, systems, equipment, and networks. Operations are governed by the “Data Operations Cycle Procedures”, the “Information and Communications Security (ICS) Organization and Management Measures”, the “Information Operations Business Continuity Plan”, and the “Personal Data Protection Management Measures”.
Information Security Management Framework
Shih Wei attaches great importance to ICS and has established a Data Security Management Team convened by the head of the IT Office, with members including a qualified information-security supervisor, dedicated Data Security personnel, department heads, and IT Office colleagues. The team regularly discusses and reviews Company-wide information-security issues.
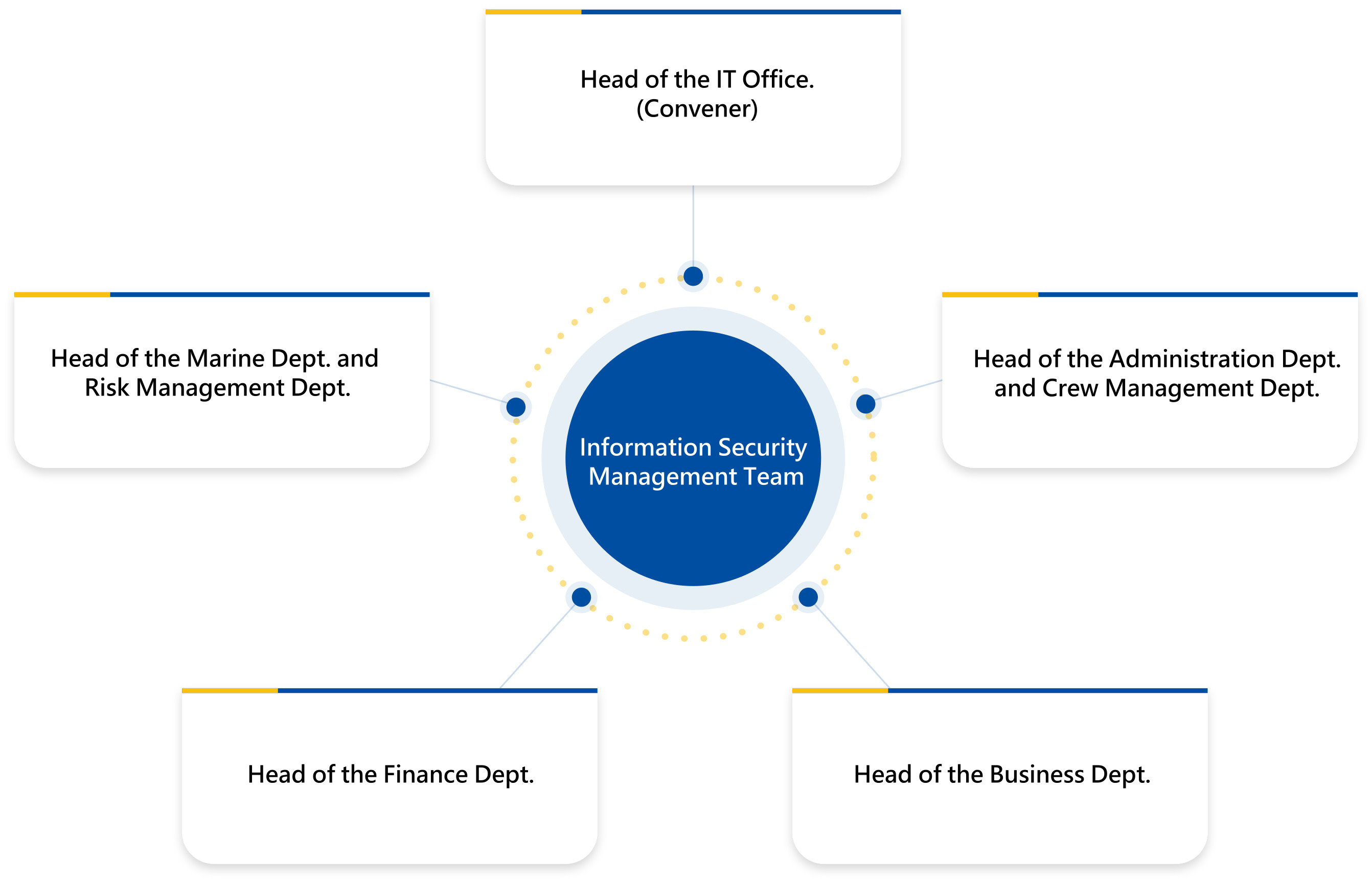
Management and Implementation Methods
In addition to annual internal audits conducted by the Auditing Office, the Company engages an ICA firm to perform an information-operations cycle review annually. We respond to the recommendations in their reports and implement improvements. Examples include:
-
Computer information and communications security control (new in the year: “Legal Software Audit Management Measures” and an internal list of permitted software for installation).
-
Personal-data and confidentiality management.
-
Strengthening overall information-systems integration (continued firewall warranty and threat-intelligence subscription support).
-
Server virtualization and cloud adoption (e.g., the employee portal and HR system), with reinforced security management.
-
Irregular sharing of data security news (five announcements) and social-engineering drills. Continued professional development for IS/IT personnel to obtain relevant certifications (one data-security certificate earned in 2024).
-
Irregular employee training (HQ self-run ICS training: 74 person-hours, 74 total participations. Information unit participation in online/onsite ICS courses or seminars: 43.5 person-hours, 3 total participations).
-
Regular restoration drills for critical systems (2 drills in 2024). Legal software audit spot checks (2 in 2024; 100% pass rate). Internal and external audits covering the information-operations cycle and ICS checks.

Customer Data and Privacy Protection
Shih Wei affords optimal protection to customer-provided data to ensure privacy. Comprehensive controls govern data access, processing, transmission, retention, and the security of personnel and equipment. Corresponding security measures are in place across applications, databases, networks, PCs, and storage media to prevent theft, loss, or leakage and safeguard customer data. In 2024, there were zero complaints concerning infringement of customer privacy or loss of customer data, and zero major information-security incidents.
In 2024, there were zero complaints concerning infringement of customer privacy or loss of customer data, and zero major information-security incidents.
Ship Information and Communication Security
The Company is committed to implementing ICS on vessels. Always-on satellite networks are deployed so that antivirus software remains up to date. Coupled with firewall controls on both the ship side and ground station, vessel network use is more secure. By the end of 2024, installation of redundant satellite links was fully completed, improving online availability and control over datasecurity management. We regularly execute sign-offs on the Data-Security Work Code and conduct incident-response drills to enhance crew responsiveness.

Investments in resources for
Information security management
In the fiscal year 2024, updates were carried out across various areas to enhance cybersecurity measures. This included updates to ship and employee computer hosts, antivirus software, email protection software and hardware maintenance, as well as updates to company websites and equipment in the data center, all aimed at continuously improving cybersecurity defenses.
By the end of 2024, installation of redundant satellite links was fully completed, improving online availability and control over data-security management.


